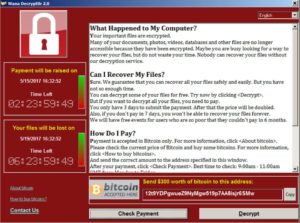
The new ransomware threat in the wild is quite amazing, but it relies on your machine having ports open to the web and the SMB service running in Windows. A lot of existing machines might have this service running and they might not be patched at all. Since this was known about for many months, I blocked port 445 on my router and my firewall long before this current news craze came about, the Wikileaks CIA tools release contained information about a port 445 exploit. This is very old news. If this service is shut down then your machine is not as susceptible to the malware as it would be if the user had a vanilla Windows machine that was more vulnerable to the exploit. There are ways to stop this from running on your machine.
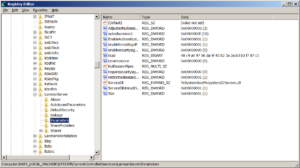
Look for this registry entry.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\LanmanServer\Parameters |
If there is a key named SMB1 in here, set the DWORD value to 00000000. My Windows 7 installation did not even have SMB1, but if it is here, disable it.
How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows and Windows Server.
This command in Windows 10 will disable the SMB service.
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol |
Scan your machine for any open ports here: https://www.grc.com/shieldsup.
Install Windows updates:
http://forum.oszone.net/thread-257198.html.
http://www.wsusoffline.net/.
Microsoft Technet guide on installing Windows updates to combat this malware.
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/.
Neither of these methods contain any telemetry or GWX related updates.
General information about Ransomware on Windows.
https://www.microsoft.com/en-us/security/portal/mmpc/shared/ransomware.aspx.
This will keep your Windows machine safe from the exploit. Not downloading shady software from websites will also help. Most download sites offer MD5 or SHA256 hashes of software downloads, this allows the user to compare the downloaded file and make sure it has not been tampered with.