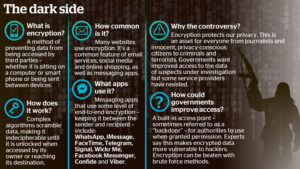
The Australian Turnbull government plans to ask encryption software developers to install back-doors in their software to enable the Police or government agencies to access the encrypted messages. Does this include GnuPG and other encryption software that is open-source? There is the PGP software, but this is now owned by Symantec and their software is now suspect. But GnuPG is good open-source encryption software and would be fine to use. Encrypted messaging has become increasingly popular among terrorist groups to plan attacks. Jailed Melbourne Anzac Day plotter Sevdet Besim used messaging app Telegram, as did the Islamic State-linked attackers killed 130 people in Paris in 2015. Australian IS poster boy Neil Prakash was a keen user of the app Surespot during his time as a recruiter and propagandist and recruiter. There are serious technical and jurisdictional challenges however. With the end-to-end encryption now commonly used by apps such WhatsApp, Facebook Messenger, Signal and Wickr Me, the companies themselves don’t have the decrypted messages. The companies are invariably based overseas, often in the United States. Therefore, the Australian government wants to have an agreement with the United States that would allow Australian authorities to ask American companies to give over the messages with a warrant.
That is what George Brandis and Malcom Turnbull want. But George Brandis does not understand technology, he is struggling to explain Internet packet routing and meta-data capture in this video. That is funny stuff, he sounds like Porky Pig. He has no idea at all about how the Internet works, or what meta-data really is. And he wants to be in control of what we look at on the Internet and wants to take over the Internet browsing of Internet users in Australia. He does not know anything about how a website address works. The IP address can change, but the hostname or domain name is the same, if you move a site to another hosting provider, you can keep the domain name. Just change the nameservers in your domain configuration. Easy. But the terrorists can use TOR or Freenet, not the main Internet, and then intercepting their Internet traffic would be harder. So what about free software options like GnuPG, would they ask them to put backdoors in their encryption package? I do not think this would work. You could download the version with the backdoor and use diff to compare it with a clean version and find the code. That is the advantage of free software.
But GnuPG developers would not go along with this for sure. Their software makes for very secure encryption and this would not be compromised by a backdoor ordered by the government. If that happened, no-one would trust it anymore and it would be forked and a clean version created. Again, because it is free software, it should be more trustworthy than closed software like PGP.