There are a few penetration testing tools that are available on Linux. One famous tool is Nmap.
Nmap
This is a port scanning tool that is capable of scanning for open ports on remote systems to test the security of that machine. This is used to test the security of a firewall or equivalent security practice to ensure that only critical ports are opened to the world. Nmap may also reveal what operating system is running on the remote machine; and what kernel version. This is important when deciding upon the attacks that will be required. Nmap may also provide information on the operating system the host is running. As well as open ports and a traceroute function.
(jcartwright@localhost) 192.168.1.5 program $ su
Password:
[root@localhost program]# nmap -A -T3 -P0 104.21.37.13
Starting Nmap 7.92 ( https://nmap.org ) at 2023-12-02 09:42 AEDT
Nmap scan report for 104.21.37.13
Host is up (0.050s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Cloudflare http proxy
|_http-title: Site doesn't have a title (text/plain; charset=UTF-8).
|_http-server-header: cloudflare
443/tcp open ssl/https cloudflare
|_http-title: 400 The plain HTTP request was sent to HTTPS port
|_http-server-header: cloudflare
8080/tcp open http Cloudflare http proxy
|_http-title: Site doesn't have a title (text/plain; charset=UTF-8).
|_http-server-header: cloudflare
8443/tcp open ssl/https-alt cloudflare
|_http-title: 400 The plain HTTP request was sent to HTTPS port
|_http-server-header: cloudflare
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Linux 5.X|4.X (87%), FreeBSD 11.X (86%)
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:4.10 cpe:/o:freebsd:freebsd:11.0
Aggressive OS guesses: Linux 5.0 - 5.4 (87%), Linux 4.10 (86%), FreeBSD 11.0-RELEASE (86%), FreeBSD 11.0-STABLE (86%), FreeBSD 11.1-STABLE (86%), FreeBSD 11.1-RELEASE (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 9 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 2.72 ms 192.168.1.1
2 21.15 ms lo10.lns41.alexeqn.nsw.vocus.network (203.134.80.19)
3 23.14 ms ae14-212.edg01.alexeqn.nsw.vocus.network (203.134.80.174)
4 21.67 ms be106-99.bdr02.syd11.nsw.vocus.network (114.31.200.184)
5 ...
6 44.53 ms be204.bdr01.akl03.akl.nz.vocus.network (114.31.202.57)
7 44.37 ms be101.bdr04.alb01.akl.nz.vocus.network (114.31.202.41)
8 44.88 ms as13335.akl.ix.nz (43.243.21.2)
9 49.12 ms 104.21.37.13
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.98 seconds
Nikto
Nikto is an open-source program that allows security scanning of a web server to find vulnerabilities in the setup of the web server and/or the software running on it.
This is very good for finding any vulnerabilities in a certain website.
(jcartwright@localhost) 192.168.1.5 program $ perl nikto.pl +host dailyadvertiser.com.au
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 13.35.147.122
+ Target Hostname: dailyadvertiser.com.au
+ Target Port: 80
+ Message: Multiple IP addresses found: 13.35.147.122, 13.35.147.101, 13.35.147.46, 13.35.147.105
+ Start Time: 2023-12-02 09:23:02 (GMT11)
---------------------------------------------------------------------------
+ Server: CloudFront
+ Retrieved via header: 1.1 55995d846c30878fb2be24f27b355ccc.cloudfront.net (CloudFront)
+ The anti-clickjacking X-Frame-Options header is not present.
+ Uncommon header 'x-amz-cf-pop' found, with contents: SYD1-C1
+ Uncommon header 'x-cache' found, with contents: Redirect from cloudfront
+ Uncommon header 'x-amz-cf-id' found, with contents: -xge1OnVfke4KSsDwD0mNh3YYhyYNqrl57uWBrQUbmiMG7ZmtUA5wA==
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type.
+ Root page / redirects to: https://dailyadvertiser.com.au/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ 8051 requests: 0 error(s) and 6 item(s) reported on remote host
+ End Time: 2023-12-02 09:26:03 (GMT11) (181 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
And this is another example.
(jcartwright@localhost) 192.168.1.5 program $ perl nikto.pl +host https://scinoticsolutions.com
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 104.21.37.13
+ Target Hostname: scinoticsolutions.com
+ Target Port: 443
---------------------------------------------------------------------------
+ SSL Info: Subject: /CN=scinoticsolutions.com
Altnames: scinoticsolutions.com, *.scinoticsolutions.com
Ciphers: TLS_AES_256_GCM_SHA384
Issuer: /C=US/O=Google Trust Services LLC/CN=GTS CA 1P5
+ Message: Multiple IP addresses found: 104.21.37.13, 172.67.202.103
+ Start Time: 2023-12-02 09:35:40 (GMT11)
---------------------------------------------------------------------------
+ Server: cloudflare
+ Uncommon header 'alt-svc' found, with contents: h3=":443"; ma=86400
+ Uncommon header 'x-turbo-charged-by' found, with contents: LiteSpeed
+ The site uses SSL and the Strict-Transport-Security HTTP header is set with max-age=0.
+ A report-to header was sent by the server, the URI is: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=mwDNMh0Uv1xGUYpnBCAXbshTQ2hexCXhGWYqRlHF5Hiik9S87OrcVqHAaarSD4hJQtnA34Hzxx5COsv9z0Q6QQl1yby%2FAItjMOFloB1BQ1qcvzLIv4aFmKEsSID5jJ8ROUG00mTp%2Bzs%3D"}],"group":"cf-nel","max_age":604800}
+ OSVDB-3268: /: Directory indexing found.
+ The Content-Encoding header is set to "deflate" this may mean that the server is vulnerable to the BREACH attack.
+ ERROR: Error limit (20) reached for host, giving up. Last error: opening stream: ssl connect failed
+ SCAN TERMINATED: 20 error(s) and 6 item(s) reported on remote host
+ End Time: 2023-12-02 09:38:14 (GMT11) (154 seconds)
---------------------------------------------------------------------------
WPScan
Wpscan allows the scanning of WordPress websites to find various vulnerabilities in the version of WordPress installed upon the webserver. If a vulnerability is found it will be listed with a URL that will give more information about the vulnerability.
(jcartwright@localhost) 192.168.1.5 bin $ ./wpscan --url https://helylegal.com.au/ --random-user-agent
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
As well as config backups on the website. These can be a gold mine. You may find database backups that can contain very good and useful data.
Here is a sample scan against a very vulnerable website, this shows how the free WPScan plan may be very useful for finding vulnerable parts of a WordPress website.
| Last Updated: 2022-12-01T16:58:00.000Z | | Found By: Urls In Homepage (Passive Detection) | | [!] 2 vulnerabilities identified: | | [!] Title: Vertical scroll recent post <= 14.0 - Contributor+ Stored Cross-Site Scripting | References: | - https://wpscan.com/vulnerability/d328d95a-106d-4747-85e4-b3f08e1818e8 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-23862 | | [!] Title: Vertical scroll recent post <= 14.0 - Cross-Site Request Forgery via vsrp_admin_options | References: | - https://wpscan.com/vulnerability/4a6d6d6e-6f88-4bee-b0ab-b02b9154e7a7 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-47671 | - https://www.wordfence.com/threat-intel/vulnerabilities/id/307bbfe6-8a57-461d-aa7d-bce962da4239 | | Version: 14.0 (80% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - https://shrishikshayatancollege.org/wp-content/plugins/vertical-scroll-recent-post/readme.txt [+] wp-whatsapp | Location: https://shrishikshayatancollege.org/wp-content/plugins/wp-whatsapp/ | Last Updated: 2023-09-11T09:21:00.000Z | [!] The version is out of date, the latest version is 3.4.6 | | Found By: Urls In Homepage (Passive Detection) | Confirmed By: Urls In 404 Page (Passive Detection) | | Version: 3.2.1 (80% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - https://shrishikshayatancollege.org/wp-content/plugins/wp-whatsapp/readme.txt [+] wps-visitor-counter | Location: https://shrishikshayatancollege.org/wp-content/plugins/wps-visitor-counter/ | Last Updated: 2021-07-03T04:42:00.000Z | [!] The version is out of date, the latest version is 1.4.8 | | Found By: Urls In Homepage (Passive Detection) | Confirmed By: Urls In 404 Page (Passive Detection) | | Version: 1.4.3 (50% confidence) | Found By: Readme - ChangeLog Section (Aggressive Detection) | - https://shrishikshayatancollege.org/wp-content/plugins/wps-visitor-counter/readme.txt [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:50 <=============================================================================================================================> (137 / 137) 100.00% Time: 00:00:50 [i] No Config Backups Found. [+] WPScan DB API OK | Plan: free | Requests Done (during the scan): 24 | Requests Remaining: 1 [+] Finished: Sat Dec 2 10:27:35 2023 [+] Requests Done: 255 [+] Cached Requests: 7 [+] Data Sent: 85.378 KB [+] Data Received: 1.632 MB [+] Memory used: 262.637 MB [+] Elapsed time: 00:02:25
Wireshark
Wireshark is a wireless scanning tool that allows the capture of all packets traveling over the network. This will be used to see what type of devices are on the network, as the contents of the packets include information on the type of router that is routing packets. This can be used to see if there are any vulnerabilities in that hardware. Researching the hardware can be used to find the default login information for that device, it could have been configured with the unchanged details and this could be used to gain better access to the network.
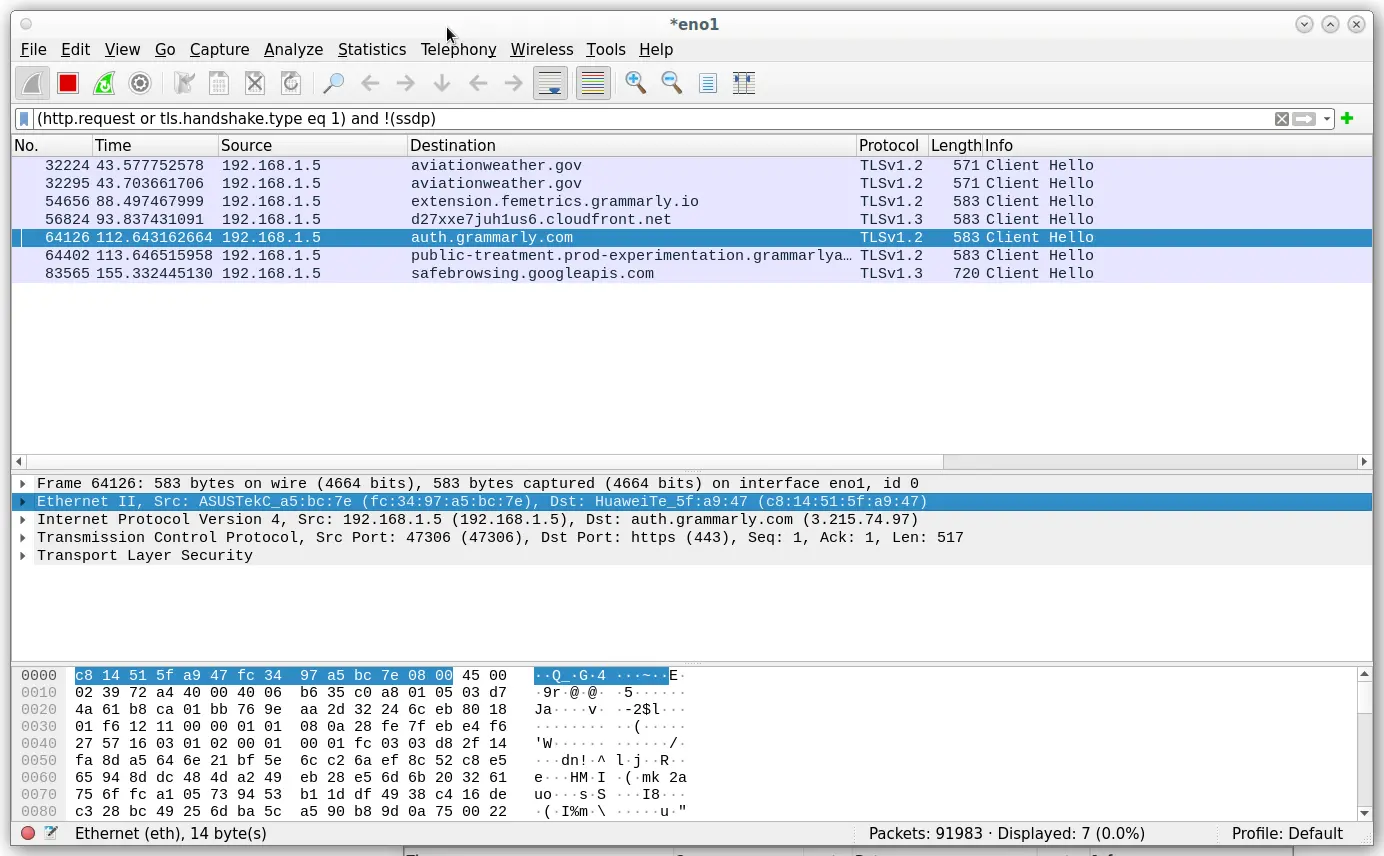
This scan will find the IP address of the PC you are using and then the Gateway it is passing through.
(http.request or tls.handshake.type eq 1) and !(ssdp)Very useful.
Lynis
Lynis is a scanning utility that will scan your system and then output a comprehensive report of the system security upon completion. This would be very nice for hardening a Linux server.
[root@localhost Desktop]# lynis audit system
[ Lynis 3.0.9 ]
################################################################################
Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are
welcome to redistribute it under the terms of the GNU General Public License.
See the LICENSE file for details about using this software.
2007-2021, CISOfy - https://cisofy.com/lynis/
Enterprise support available (compliance, plugins, interface and tools)
################################################################################
[+] Initializing program
------------------------------------
- Detecting OS... [ DONE ]
- Checking profiles... [ DONE ]
---------------------------------------------------
Program version: 3.0.9
Operating system: Linux
Operating system name: AlmaLinux 9.3 (Shamrock Pampas Cat)
Operating system version: 9.3
Kernel version: 5.14.0
Hardware platform: x86_64
Hostname: localhost
---------------------------------------------------
Profiles: /etc/lynis/default.prf
Log file: /var/log/lynis.log
Report file: /var/log/lynis-report.dat
Report version: 1.0
Plugin directory: /usr/share/lynis/plugins
---------------------------------------------------
Auditor: [Not Specified]
Language: en
Test category: all
Test group: all
---------------------------------------------------
- Program update status... [ SKIPPED ]
[+] System tools
------------------------------------
- Scanning available tools...
- Checking system binaries...
[+] Plugins (phase 1)
------------------------------------
Note: plugins have more extensive tests and may take several minutes to complete
- Plugins enabled [ NONE ]
[+] Boot and services
------------------------------------
- Service Manager [ systemd ]
- Checking UEFI boot [ ENABLED ]
- Checking Secure Boot [ DISABLED ]
- Checking presence GRUB2 [ FOUND ]
- Checking for password protection [ OK ]
- Check running services (systemctl) [ DONE ]
Result: found 40 running services
- Check enabled services at boot (systemctl) [ DONE ]
Result: found 54 enabled services
- Check startup files (permissions) [ OK ]
- Running 'systemd-analyze security'
- ModemManager.service: [ MEDIUM ]
- NetworkManager.service: [ EXPOSED ]
- accounts-daemon.service: [ UNSAFE ]
- alsa-state.service: [ UNSAFE ]
- atd.service: [ UNSAFE ]
- auditd.service: [ EXPOSED ]
- avahi-daemon.service: [ UNSAFE ]
- chronyd.service: [ PROTECTED ]
- colord.service: [ EXPOSED ]
- crond.service: [ UNSAFE ]
- cups.service: [ UNSAFE ]
- dbus-broker.service: [ EXPOSED ]
- dm-event.service: [ UNSAFE ]
- emergency.service: [ UNSAFE ]
- firewalld.service: [ UNSAFE ]
- gdm.service: [ UNSAFE ]
- [email protected]: [ UNSAFE ]
- gssproxy.service: [ UNSAFE ]
- httpd.service: [ UNSAFE ]
- irqbalance.service: [ EXPOSED ]
- iscsid.service: [ UNSAFE ]
- iscsiuio.service: [ UNSAFE ]
- libstoragemgmt.service: [ UNSAFE ]
- libvirtd.service: [ UNSAFE ]
- low-memory-monitor.service: [ MEDIUM ]
- lvm2-lvmpolld.service: [ UNSAFE ]
- mcelog.service: [ UNSAFE ]
- mdatp.service: [ UNSAFE ]
- mde_netfilter.service: [ EXPOSED ]
- mdmonitor.service: [ UNSAFE ]
- mlocate-updatedb.service: [ EXPOSED ]
- multipathd.service: [ UNSAFE ]
- nfs-idmapd.service: [ UNSAFE ]
- nfs-mountd.service: [ UNSAFE ]
- nfsdcld.service: [ UNSAFE ]
- packagekit.service: [ UNSAFE ]
- php-fpm.service: [ UNSAFE ]
- plymouth-start.service: [ UNSAFE ]
- polkit.service: [ UNSAFE ]
- power-profiles-daemon.service: [ EXPOSED ]
- rc-local.service: [ UNSAFE ]
- rescue.service: [ UNSAFE ]
- rpc-gssd.service: [ UNSAFE ]
- rpc-statd-notify.service: [ UNSAFE ]
- rpc-statd.service: [ UNSAFE ]
- rpcbind.service: [ UNSAFE ]
- rsyslog.service: [ MEDIUM ]
- rtkit-daemon.service: [ MEDIUM ]
- smartd.service: [ UNSAFE ]
- sshd.service: [ UNSAFE ]
- sssd-kcm.service: [ EXPOSED ]
- sssd.service: [ EXPOSED ]
- switcheroo-control.service: [ EXPOSED ]
- systemd-ask-password-console.service: [ UNSAFE ]
- systemd-ask-password-plymouth.service: [ UNSAFE ]
- systemd-ask-password-wall.service: [ UNSAFE ]
- systemd-initctl.service: [ UNSAFE ]
- systemd-journald.service: [ PROTECTED ]
- systemd-logind.service: [ PROTECTED ]
- systemd-machined.service: [ MEDIUM ]
- systemd-rfkill.service: [ UNSAFE ]
- systemd-udevd.service: [ MEDIUM ]
- tuned.service: [ UNSAFE ]
- udisks2.service: [ UNSAFE ]
- upower.service: [ PROTECTED ]
- [email protected]: [ UNSAFE ]
- vgauthd.service: [ UNSAFE ]
- virtinterfaced.service: [ UNSAFE ]
- virtlockd.service: [ UNSAFE ]
- virtlogd.service: [ UNSAFE ]
- virtnetworkd.service: [ UNSAFE ]
- virtnodedevd.service: [ UNSAFE ]
- virtnwfilterd.service: [ UNSAFE ]
- virtproxyd.service: [ UNSAFE ]
- virtqemud.service: [ UNSAFE ]
- virtsecretd.service: [ UNSAFE ]
- virtstoraged.service: [ UNSAFE ]
- vmtoolsd.service: [ UNSAFE ]
- vmware-USBArbitrator.service: [ UNSAFE ]
- vmware.service: [ UNSAFE ]
- wpa_supplicant.service: [ UNSAFE ]
[+] Kernel
------------------------------------
- Checking default runlevel [ runlevel 5 ]
- Checking CPU support (NX/PAE)
CPU support: PAE and/or NoeXecute supported [ FOUND ]
- Checking kernel version and release [ DONE ]
- Checking kernel type [ DONE ]
- Checking loaded kernel modules [ DONE ]
Found 125 active modules
- Checking Linux kernel configuration file [ FOUND ]
- Checking default I/O kernel scheduler [ NOT FOUND ]
- Checking core dumps configuration
- configuration in systemd conf files [ DEFAULT ]
- configuration in /etc/profile [ DEFAULT ]
- 'hard' configuration in /etc/security/limits.conf [ DEFAULT ]
- 'soft' configuration in /etc/security/limits.conf [ DEFAULT ]
- Checking setuid core dumps configuration [ PROTECTED ]
- Check if reboot is needed [ NO ]
[+] Memory and Processes
------------------------------------
- Checking /proc/meminfo [ FOUND ]
- Searching for dead/zombie processes [ NOT FOUND ]
- Searching for IO waiting processes [ NOT FOUND ]
- Search prelink tooling [ NOT FOUND ]
[+] Users, Groups and Authentication
------------------------------------
- Administrator accounts [ OK ]
- Unique UIDs [ OK ]
- Consistency of group files (grpck) [ WARNING ]
- Unique group IDs [ OK ]
- Unique group names [ OK ]
- Password file consistency [ OK ]
- Password hashing methods [ SUGGESTION ]
- Checking password hashing rounds [ DISABLED ]
- Query system users (non daemons) [ DONE ]
- NIS+ authentication support [ NOT ENABLED ]
- NIS authentication support [ NOT ENABLED ]
- Sudoers file(s) [ FOUND ]
- Permissions for directory: /etc/sudoers.d [ OK ]
- Permissions for: /etc/sudoers [ OK ]
- PAM password strength tools [ OK ]
- PAM configuration file (pam.conf) [ NOT FOUND ]
- PAM configuration files (pam.d) [ FOUND ]
- PAM modules [ FOUND ]
- LDAP module in PAM [ NOT FOUND ]
- Accounts without expire date [ SUGGESTION ]
- Accounts without password [ OK ]
- Locked accounts [ OK ]
- Checking user password aging (minimum) [ DISABLED ]
- User password aging (maximum) [ CONFIGURED ]
- Checking expired passwords [ FOUND ]
- Checking Linux single user mode authentication [ OK ]
- Determining default umask
- umask (/etc/profile) [ NOT FOUND ]
- umask (/etc/login.defs) [ SUGGESTION ]
- LDAP authentication support [ NOT ENABLED ]
- Logging failed login attempts [ DISABLED ]
[+] Shells
------------------------------------
- Checking shells from /etc/shells
Result: found 8 shells (valid shells: 8).
- Session timeout settings/tools [ NONE ]
- Checking default umask values
- Checking default umask in /etc/bashrc [ WEAK ]
- Checking default umask in /etc/csh.cshrc [ WEAK ]
- Checking default umask in /etc/profile [ NONE ]
[+] File systems
------------------------------------
- Checking mount points
- Checking /home mount point [ OK ]
- Checking /tmp mount point [ SUGGESTION ]
- Checking /var mount point [ SUGGESTION ]
- Checking LVM volume groups [ FOUND ]
- Checking LVM volumes [ FOUND ]
- Query swap partitions (fstab) [ OK ]
- Testing swap partitions [ OK ]
- Testing /proc mount (hidepid) [ SUGGESTION ]
- Checking for old files in /tmp [ OK ]
- Checking /tmp sticky bit [ OK ]
- Checking /var/tmp sticky bit [ OK ]
- ACL support root file system [ ENABLED ]
- Mount options of / [ OK ]
- Mount options of /boot [ DEFAULT ]
- Mount options of /dev [ PARTIALLY HARDENED ]
- Mount options of /dev/shm [ PARTIALLY HARDENED ]
- Mount options of /home [ DEFAULT ]
- Mount options of /run [ HARDENED ]
- Total without nodev:11 noexec:16 nosuid:8 ro or noexec (W^X): 16 of total 34
- Checking Locate database [ FOUND ]
- Disable kernel support of some filesystems
LOL those are so goddamned antiquated it’s not even funny. Look up Project Discovery. Replace your old shit with new shit. OMFG