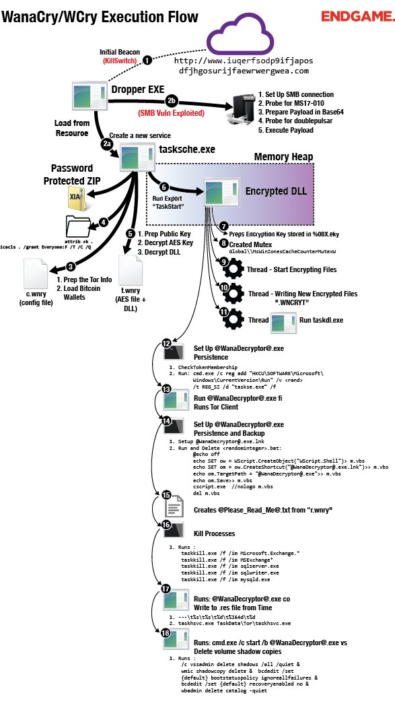
This is the execution flow for the Wannacry malware. This ransomware can encrypt all of your files and then demand payment in bitcoins to decrypt the files. The virus was recently remade into a 2.0 with no killswitch. But the older version is this one that had a killswitch that contacted a website that did not exist, and if it did, the ransomware would not run. Another variant that was part of EternalBlue that silently mines cryptocurrency called Adylkuzz was released, this is a new media craze, obsessing about Internet security and the need for greater controls on the flow of information to keep us safe from Internet nasties. There are Windows Updates to fix this, but locking down your router and Windows machine is another way to be safe from this ransomware. The leaked NSA tools could have assisted in the creation of this exploit. But blaming North Korea is a bit much, there is no proof that they even did this, IP addresses can be spoofed with a VPN and/or a proxy. The killswitch for the ransomware was the website address www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, which did not exist until a security researcher created it. This was the address that stopped the malware program from doing it`s job.
An analysis of the malware may be found here: https://www.youtube.com/watch?v=d_j8UUQbJsc. A good look at the internals of the program. Go here to find more information and to download a sample of the ransomware. Dangerous though. Best to use a Linux machine to handle this code. Good to be able to handle the file in a safe environment.
I have made a dump of the wannacry sample, using objdump. Get it here: http://www.securitronlinux.com/arma3/objdump.txt.
Some more information.
localhost% objdump -f ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.bin ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.bin: file format pei-i386 architecture: i386, flags 0x0000010a: EXEC_P, HAS_DEBUG, D_PAGED start address 0x004077ba |
SHA256 hash: ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
Forensic analysis of the intrusion: http://freports.us.checkpoint.com/wannacryptor2_1/ep-complete.html.