Social Networking is taking over the web and changing the world forever, introducing a new paradigm, where your whole life is stored in a massive data centre and even if you try to erase your history, it is hard to do, you need to do heaps of Google searching and try to delete as much of it as possible to clean up your image, say you are going for a job and the prospective employer will search your name on Google and see what kind of a person you are, I have had this happen myself, I went for a job, an engineering position and the employer was using Google to search for `John Cartwright engineer`, he was seeing what kind of work history I had. But if you have unpleasant pictures of yourself online, this would not work in your favour. Plenty of people have funny pictures on Facebook or MySpace that would not look good to an employer. The other online platforms like 4chan are Anonymous, but I would not count on actually getting away with posting the wrong thing. That is what you must be careful of. 4chan does archive posts and they will be online forever unless you request to have them deleted, which can be done.
That is why you must be careful what you post on the Internet if you want to be seen in a good light and not have some prospective employer seeing the photos from your drunken party they might be funny at the time, but if they see them they would be pretty embarrassing. Especially if they are very compromising photos. That is my case for online anonymity, it is the best avenue for discussion, (and trolling), there is, you would be amazed what people will post when they are Anonymous. With some governments pushing for real names in IRC, and Blizzard wanting real-id on their forums, is this the death of online security and privacy? The government wants to have everyone posting under their real name to control and monitor what is being posted. What are they worried about if they are not doing anything behind the scenes that they would not want people talking about? But stay Anonymous and stay cool. Sure, have a Facebook page if you want to, but take a good look at a photo before posting it. It is better to have a positive online profile and this will look good in the future when you are older and wiser, then you will not have those embarrassing photographs haunting you.
This is really what we are using our super fast modern computers for? The history of modern computing technology goes back to ancient Greece, with the Ankithera machine which was an Astronomical calculator to compute the positions of the planets. More recently, Blaise Pascal (1623 – 1662) of France invented the computing machine to perform various calculations which were followed by Gottfried Wilhelm Leibniz (1646 – 1716) of Germany and the arguably most famous of all, Charles Babbage (1792 – 1871) of England. Who built the difference engine to perform calculations and output the results with the positions of gears and inputting the data mechanically to program the machine? Charles Babbage envisioned a machine that could output on paper that would be able to save a hard copy of the data. This would allow transcribing errors to be eliminated with proofreading. The way each machine worked improved as each was invented, Pascal’s machine was built to follow only the addition algorithm.

With the advent of transistors, and the phasing out of vacuum tubes in 1960 computers could become much smaller and pack more processing power into a smaller space, this was the dawn of the second-generation computer. Then in 1965 integrated circuits appeared in computers followed by large-scale integration of components into a single chip appeared in the early 1970s. This was the beginning of a new era in computing, with the result being Apple computers allowing a machine not much bigger than a small suitcase. This of course resulted in the advent of the laptop computer, one of which I am using to type this posting. The book I am paraphrasing this information out of Data Processing 2nd edition, ISBN -0534-98042-2 mentions the practice of cryogenically cooling a CPU to allow it to run much faster but using liquid Helium to cool the CPU to -459.69 degrees Fahrenheit. This is based on a theory by Brian Josephson that the speed of electrical switching can speed up as the temperature of the CPU approaches absolute zero. The writers of this book, applying the theory to CPUs of the early 80s have predicted CPUs with nanosecond access times by the late 1980s. Sure modern Core 2 Duo and Core i7 CPU’s are fast, but each core still has to wait for the other core to finish before it can execute its action.
Simply put only one core in a CPU can be running action at any time. They cannot be running simultaneously. You need a Asynchronous CPU for that. I would love to have a Quantum PC though, with about 16000 qubits. Sex on a chip. The First stored program was on the EDSAC computer, built at Cambridge University in 1949, not long after the end of the Second World War. Magnetic Core memory was used in the ENIAC computer in a limited fashion, but came into prominence with the IBM 704 computer with 32K words, in 1955.
Consequently, the appropriate sequence of steps was embedded into the structure of the machine itself. In a similar fashion, Leibniz’s machine also had its algorithms embedded into its structure. However, Leibniz’s machine offered a variety of arithmetic operations from which the operator could select. Finally, Babbage’s machine allowed the user to use punched cards to program the sequence of steps the machine was to perform into the machine and have a stockpile of ready programmed cards ready to hand to perform any calculation desired. The idea of punched cards goes back to 1801, Joseph Jacquard used a similar technique for controlling weaving looms in France. These machines are considered algorithmic machines versus numeric calculators and are not normally mentioned in computing history. The advances in technology led to workers smashing the looms, as they feared losing their jobs to technology. Nowadays, we have robots that can do the work of humans, and many jobs could be obsolete in the future. it is not necessary for people to pick fruit and seeds, robots can do this without tiring and without strikes for better conditions. Or complaining about the weather.
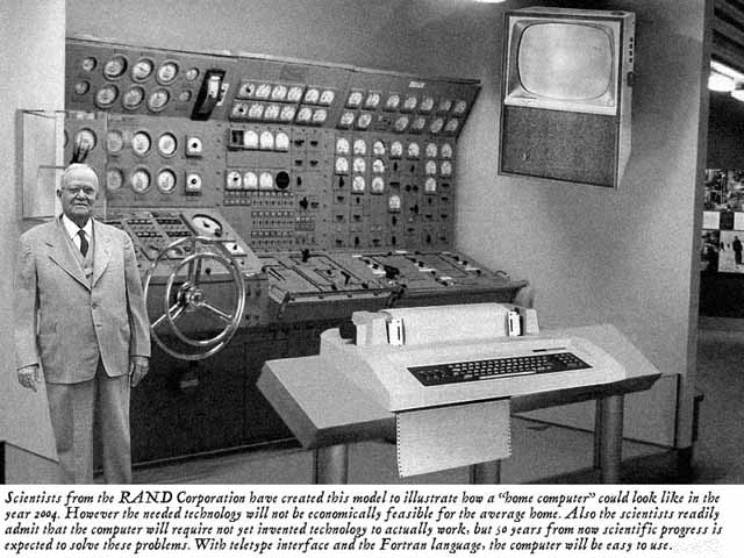
The real computing age really began when the Mark 1 computer was built in 1944, using electronically controlled relays. This was an electromechanical computer not a fully solid-state computer like the ones we have now. And it took up a whole room, like the ENIAC (Electronic Numerical Calculator And Computer) which used vacuum tubes instead of modern Transistors to perform calculations. This was the first fully electronic computer to be built, then the invention of the transistor allowed even smaller machines to be built with significantly more computing power than the Mark 1 which would fit in a box on a desktop. The 8086 computer seems pretty slow these days, but it was the fastest machine of its time in 1978, the year I was born! The Tandy 1000 desktop computer was the first desktop machine I really used, before that, I had used a computer with a cassette tape drive to load programs off music cassettes tapes.
They were fun when you played them in an audio tape player. The Tandy 1000 runs at 4.77 Megahertz. That is a beast. You could plug a TV screen into the composite input and use a TV as a monitor although the picture quality would not be as good. I remember that my dad was using an older version of a Tandy computer on his machine and I could tune in to the TV in my room across the house and see what he was working on. I have heard about monitoring what is on a CRT screen in a modern machine by capturing the radiation emitted from the screen. But if you have an underground hacking dungeon with an earthed copper Faraday cage then you will be safe. Or a TFT/LCD screen. If you have a device to enable TEMPEST snooping then you can read monitor displays at 300 yards range by re-constructing the screen from the electromagnetic emissions from the screen. This is very Elite black hat stuff used by the government to snoop on people from a distance.