SSL packets sent to and fro from your machine can contain a lot of useful information. I am going to show how to see what websites are visited on a network. Firstly, load Wireshark and then listen to traffic on your machine. Then visit a few different websites with Firefox or Chrome.
Use this filter to filter for the Client Hello packets we need.
ssl.handshake.extensions_server_name |
Click a Client Hello packet, then click Secure Sockets Layer -> TLSv1.2 Record Layer: Handshake Protocol: Client Hello -> Handshake Protocol: Client Hello -> Extension: server_name (len=24) -> Server Name Indication extension. This will contain the server name that was visited by the web user.
It should look like this when you are done. This is how to know what web addresses a user is browsing on your network.
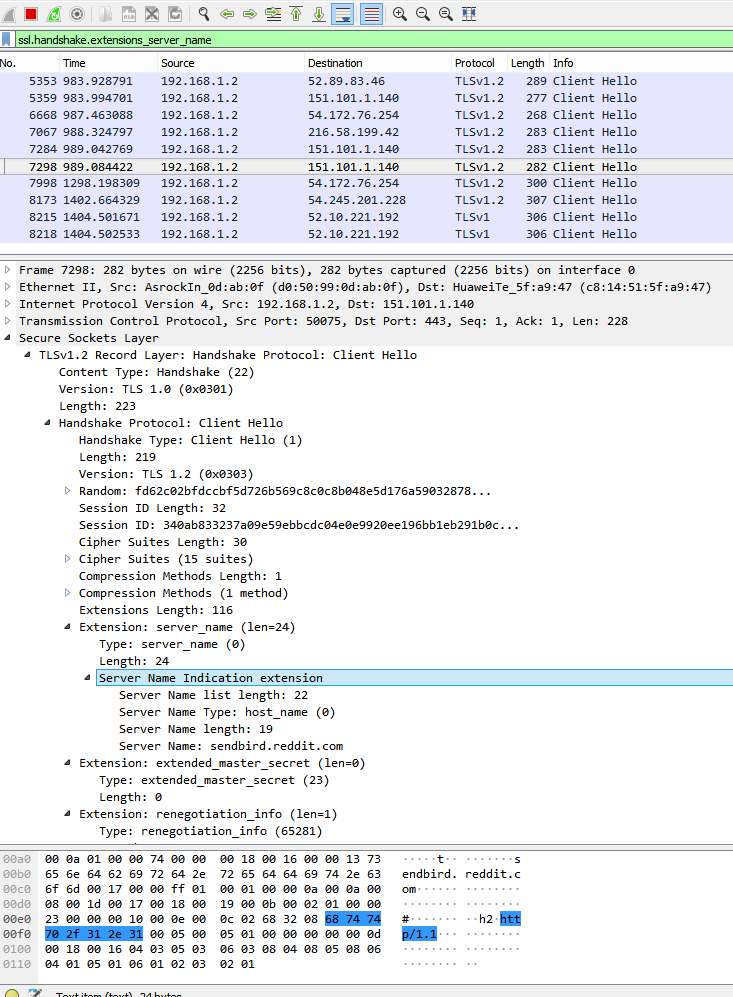
So, using HTTPS does not hide all web traffic from someone who wants to snoop on your network and see everything visit on it. This also shows other domains used by the parent domain, like a CDN to load images. Very interesting indeed. I think the only way around this is to use an encrypted VPN tunnel to browse the Internet.
Here is an example dump of web traffic that shows the contents of the TLSv1.2 Record Layer: Handshake Protocol: Client Hello packet.
0000 01 00 00 f3 03 03 77 fe a3 53 5f 87 b0 24 5a c4 ...ó..wþ£S_.°$ZÄ 0010 12 2f 66 6c af 8c 07 e8 69 b7 e9 d1 a8 80 8a 08 ./fl¯..èi·éѨ... 0020 25 93 e0 ac c4 33 20 54 ec c7 eb 2f bd ba bf 32 %.à¬Ä3 TìÇë/½º¿2 0030 98 e2 f4 46 ba f5 63 10 9b fa da 24 ad 90 7a 5b .âôFºõc..úÚ$..z[ 0040 6b 5c 21 c6 4d 85 f6 00 1e c0 2b c0 2f cc a9 cc k\!ÆM.ö..À+À/Ì©Ì 0050 a8 c0 2c c0 30 c0 0a c0 09 c0 13 c0 14 00 33 00 ¨À,À0À.À.À.À..3. 0060 39 00 2f 00 35 00 0a 01 00 00 8c 00 00 00 30 00 9./.5.........0. 0070 2e 00 00 2b 77 65 62 65 78 74 65 6e 73 69 6f 6e ...+webextension 0080 73 2e 73 65 74 74 69 6e 67 73 2e 73 65 72 76 69 s.settings.servi 0090 63 65 73 2e 6d 6f 7a 69 6c 6c 61 2e 63 6f 6d 00 ces.mozilla.com. 00a0 17 00 00 ff 01 00 01 00 00 0a 00 0a 00 08 00 1d ...ÿ............ 00b0 00 17 00 18 00 19 00 0b 00 02 01 00 00 23 00 00 .............#.. 00c0 00 10 00 0e 00 0c 02 68 32 08 68 74 74 70 2f 31 .......h2.http/1 00d0 2e 31 00 05 00 05 01 00 00 00 00 00 0d 00 18 00 .1.............. 00e0 16 04 03 05 03 06 03 08 04 08 05 08 06 04 01 05 ................ 00f0 01 06 01 02 03 02 01 ....... |
This is how easy it is to find web addresses from SSL traffic. I hope you find this to be very useful and find a way to make use of this when penetration testing or just snooping… The “Statistics” -> “HTTP” -> “Requests” menu option opens a window that shows downloaded files, but this shows ALL files requested from websites.
Overall, this is a very good trick and could be very useful to find out the habits of a target, when building a profile on them to find out which bank they use, or what favorite websites they have. Good for social engineering purposes.
To find out if a user has searched on a website, use something like this.
http.request.uri contains "s=ssh" and http.host== securitronlinux.com |
You cannot use this to find Google searches, as they are encrypted.